Docker Registry in Nexus
This article describes the steps to deploy the external Docker registry in the designated Nexus server.
Download the Nexus repository.
# wget -P /etc/yum.repos.d/ https://repo.sonatype.com/repository/community-hosted/rpm/sonatype-community.repoInstall the following software packages.
# yum install docker wget -yDeploy and start the Nexus software.
# yum install nexus-repository-manager # systemctl start nexus-repository-managerCreate the SSL certificates on the server based on the description highlighted in this link. The following
nexus.crtcertificate will be used during CDP PvC Data Services installation.# keytool -genkeypair -keystore keystore.jks -storepass password -alias jetty -keyalg RSA -keysize 2048 -validity 5000 -keypass password -dname 'CN=nexus.cdpkvm.cldr, OU=Sonatype, O=Sonatype, L=Unspecified, ST=Unspecified, C=SG' -ext 'SAN=DNS:nexus.cdpkvm.cldr' -ext "BC=ca:true" # keytool -exportcert -keystore keystore.jks -alias jetty -rfc > nexus.crt # keytool -importkeystore -srckeystore keystore.jks -destkeystore nexus.p12 -deststoretype PKCS12 # openssl pkcs12 -nokeys -in nexus.p12 -out nexus.pem # openssl pkcs12 -nocerts -nodes -in nexus.p12 -out nexus.keyCopy the JKS file to
/opt/sonatype/sonatype-work/nexus3/etc/ssl/directory.# cp keystore.jks /opt/sonatype/sonatype-work/nexus3/etc/ssl/Check that the hostname is correctly defined in the certificate.
# openssl x509 -noout -text -in nexus.crt | grep -A1 X509v3 X509v3 extensions: X509v3 Basic Constraints: CA:TRUE X509v3 Subject Alternative Name: DNS:nexus.cdpkvm.cldr X509v3 Subject Key Identifier: 08:BF:E3:9F:53:50:0A:57:B5:BB:1E:E4:5A:D2:4E:0F:E1:10:5D:11Configure the
/opt/sonatype/nexus3/etc/jetty/jetty-https.xmlfile. Sample is shown as follows.<New id="sslContextFactory" class="org.eclipse.jetty.util.ssl.SslContextFactory$Server"> <Set name="certAlias">jetty</Set> <Set name="KeyStorePath"><Property name="ssl.etc"/>/keystore.jks</Set> <Set name="KeyStorePassword">password</Set> <Set name="KeyManagerPassword">password</Set> <Set name="TrustStorePath"><Property name="ssl.etc"/>/keystore.jks</Set> <Set name="TrustStorePassword">password</Set> <Set name="EndpointIdentificationAlgorithm"></Set> <Set name="NeedClientAuth"><Property name="jetty.ssl.needClientAuth" default="false"/></Set> <Set name="WantClientAuth"><Property name="jetty.ssl.wantClientAuth" default="false"/></Set> <Set name="IncludeProtocols"> <Array type="java.lang.String"> <Item>TLSv1.2</Item> </Array> </Set> </New>Configure the
/opt/sonatype/sonatype-work/nexus3/etc/nexus.propertiesfile. Sample is shown below.# Jetty section # application-port=8081 # application-host=0.0.0.0 # nexus-args=${jetty.etc}/jetty.xml,${jetty.etc}/jetty-http.xml,${jetty.etc}/jetty-requestlog.xml nexus-args=${jetty.etc}/jetty.xml,${jetty.etc}/jetty-http.xml,${jetty.etc}/jetty-https.xml,${jetty.etc}/jetty-requestlog.xml # nexus-context-path=/ # Nexus section # nexus-edition=nexus-pro-edition # nexus-features=\ # nexus-pro-feature # nexus.hazelcast.discovery.isEnabled=true application-port-ssl=8443 ssl.etc=${karaf.data}/etc/sslRestart the Nexus service.
# systemctl restart nexus-repository-managerLog in to the Nexus portal
https://nexus.cpdkvm.cldr:8443
Setup the Docker repository with SSL port. In this demo, the SSL-enabled docker repository URL is
https://nexus.cdpkvm.cldr:9999/cdppvc.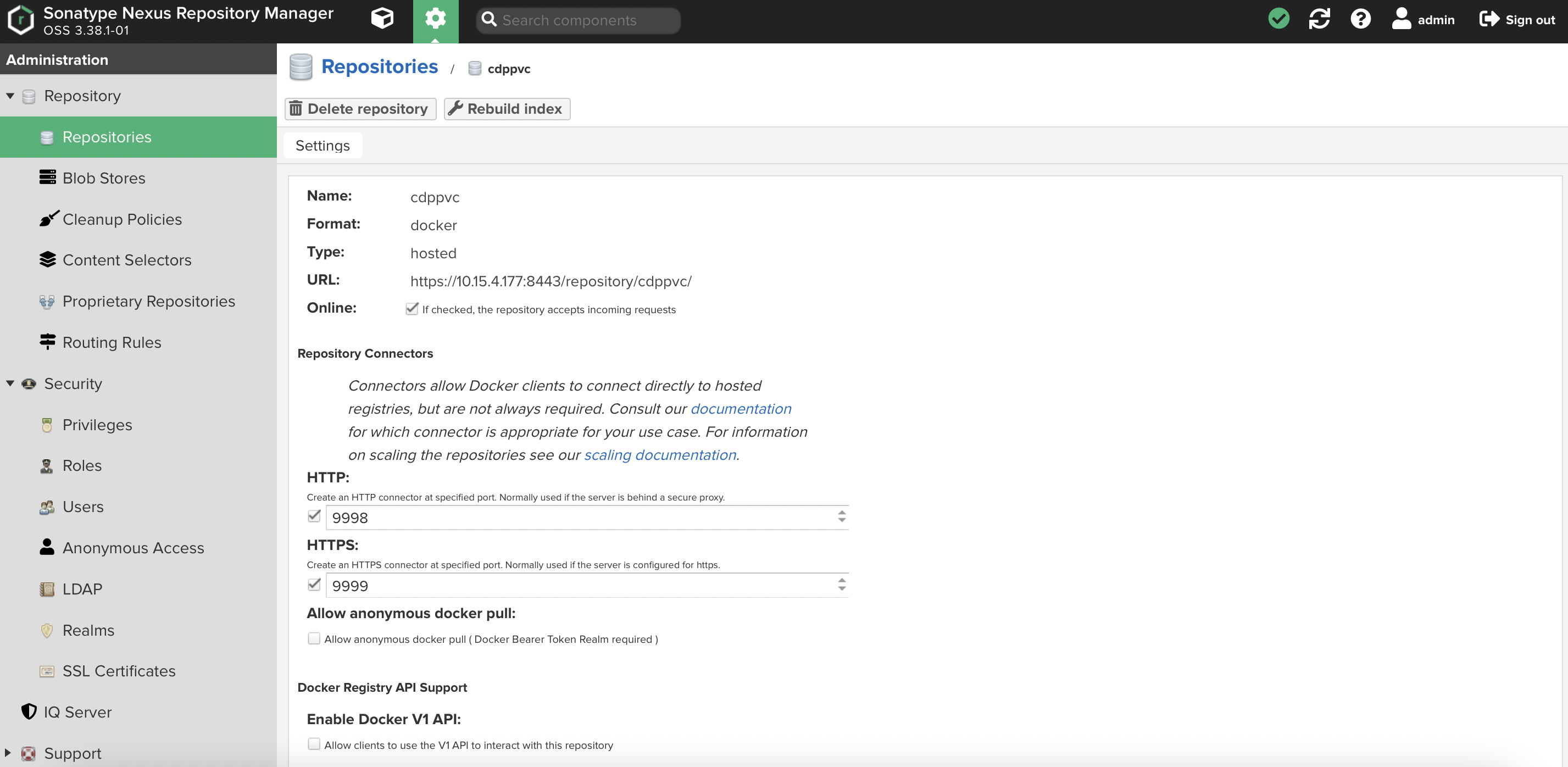
Ensure that the port SSL port 9999 is up and running.
# netstat -an | grep 999 tcp 0 0 0.0.0.0:9998 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:9999 0.0.0.0:* LISTENTest the SSL Docker URL. Note that an error “SEC_ERROR_UNTRUSTED_ISSUER” has occured.
# curl -v -u admin:admin "https://nexus.cdpkvm.cldr:9999/v2/_catalog" * About to connect() to nexus.cdpkvm.cldr port 9999 (#0) * Trying 10.15.4.177... * Connected to nexus.cdpkvm.cldr (10.15.4.177) port 9999 (#0) * Initializing NSS with certpath: sql:/etc/pki/nssdb * CAfile: /etc/pki/tls/certs/ca-bundle.crt CApath: none * Server certificate: * subject: CN=nexus.cdpkvm.cldr,OU=Sonatype,O=Sonatype,L=Unspecified,ST=Unspecified,C=SG * start date: Jun 25 12:33:15 2022 GMT * expire date: Mar 03 12:33:15 2036 GMT * common name: nexus.cdpkvm.cldr * issuer: CN=nexus.cdpkvm.cldr,OU=Sonatype,O=Sonatype,L=Unspecified,ST=Unspecified,C=SG * NSS error -8172 (SEC_ERROR_UNTRUSTED_ISSUER) * Peer's certificate issuer has been marked as not trusted by the user. * Closing connection 0 curl: (60) Peer's certificate issuer has been marked as not trusted by the user. More details here: http://curl.haxx.se/docs/sslcerts.html curl performs SSL certificate verification by default, using a "bundle" of Certificate Authority (CA) public keys (CA certs). If the default bundle file isn't adequate, you can specify an alternate file using the --cacert option. If this HTTPS server uses a certificate signed by a CA represented in the bundle, the certificate verification probably failed due to a problem with the certificate (it might be expired, or the name might not match the domain name in the URL). If you'd like to turn off curl's verification of the certificate, use the -k (or --insecure) option.Update the CA cert (nexus.crt) in the truststore of the server.
# cp nexus.crt /etc/pki/ca-trust/source/anchors/ # update-ca-trust extractCheck that the CA cert has succesfully been imported into the truststore of the server.
# openssl crl2pkcs7 -nocrl -certfile /etc/pki/tls/certs/ca-bundle.crt | openssl pkcs7 -print_certs | grep subject | grep nexus subject=/C=SG/ST=Unspecified/L=Unspecified/O=Sonatype/OU=Sonatype/CN=nexus.cdpkvm.cldrYou may now curl the SSL-enabled Docker URL successfully.
# curl -u admin:admin "https://nexus.cdpkvm.cldr:9999/v2/_catalog" | jq % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 100 9711 100 9711 0 0 69165 0 --:--:-- --:--:-- --:--:-- 69364 { "repositories": [Perform a test to ensure that you can login and pull the image from the Cloudera repository.
# docker login https://nexus.cdpkvm.cldr:9999/cdppvc --username admin --password admin Login Succeeded # docker image ls REPOSITORY TAG IMAGE ID CREATED SIZE # docker pull nexus.cdpkvm.cldr:9999/cdppvc/cloudera_thirdparty/fluent-bit:v1.4.6-3896242 Trying to pull repository nexus.cdpkvm.cldr:9999/cdppvc/cloudera_thirdparty/fluent-bit ... v1.4.6-3896242: Pulling from nexus.cdpkvm.cldr:9999/cdppvc/cloudera_thirdparty/fluent-bit f4816e38b7e0: Pull complete 7c949fdfdbff: Pull complete f949750d27a4: Pull complete fe54547c530b: Pull complete Digest: sha256:d3d7a16bc8f3eb5782efde9b79945eeb5c67119361e1d8daf31f7421d795ff5f Status: Downloaded newer image for nexus.cdpkvm.cldr:9999/cdppvc/cloudera_thirdparty/fluent-bit:v1.4.6-3896242 # docker image ls REPOSITORY TAG IMAGE ID CREATED SIZE nexus.cdpkvm.cldr:9999/cdppvc/cloudera_thirdparty/fluent-bit v1.4.6-3896242 a5d1d3a3a3ef 2 years ago 220 MBFor CDP PvC Data Services on Openshift platform, import the CA certificate
nexus.crtinto the Openshift platform using this method. This step is needed to prevent “x509: certificate signed by unknown authority” issue when the system attempts to pull the docker images from the above Docker registry in the process of provisioning the CDP Data Services Control Plane pods.